Improving SOC Alerting and Real-time Threat Analysis by Own Exploits
Students will exploit a vulnerable WordPress installation. This task will bring them yet another step closer to a real-world penetration testing scenario. They will implement alerts in Kibana before performing their assessments. This implementation will allow students to see dashboard alerts in real time. After completing the alerting and penetration testing portions of the project, they will use Wireshark to capture and analyze live traffic on the virtual network.
In this project, you will act as a security engineer supporting an organization’s SOC infrastructure. The SOC analysts have noticed some discrepancies with alerting in the Kibana system and the manager has asked the security engineering team to investigate and confirm that newly created alerts are working. If the alerts are working, you will then monitor live traffic on the wire to detect any abnormalities that aren’t reflected in the alerting system. Then, you will report back your findings to the manager with appropriate analysis.
Play the role of Security Engineer for X-CORP, supporting the SOC infrastructure. The SOC Analysts have noticed some discrepancies with alerting in the Kibana system and the manager has asked the Security Engineering team to investigate and confirm that newly created alerts are working. If the alerts are working, the engineers are to monitor live traffic on the wire to detect any abnormalities that aren’t reflected in the alerting system. They need to report back all their findings to the manager with appropriate analysis.
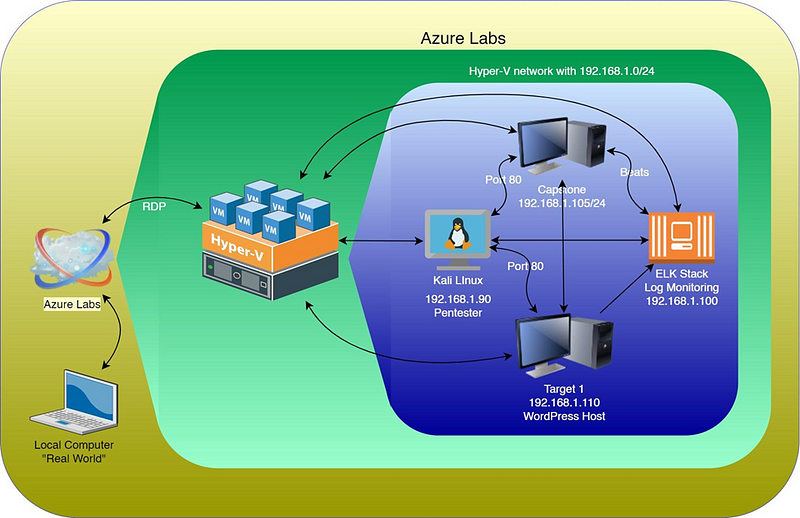
Network Topology & Critical Vulnerabilities
Our assessment uncovered the following critical vulnerabilities in Target 1.
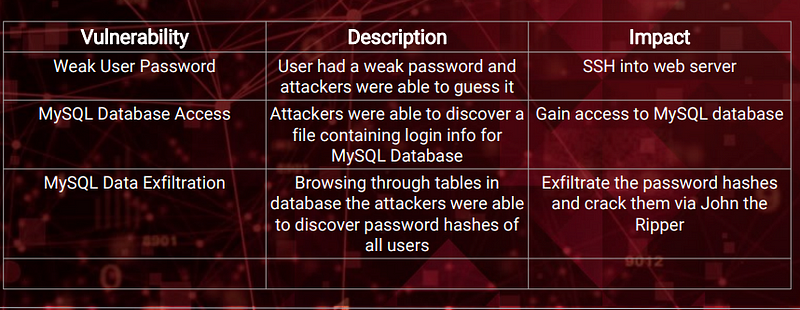
Exploits Used
Exploitation: Weak User Password (Target 1)
Summarize the following:
● How did you exploit the vulnerability? -Michael had his own name as his password and was easy to guess.
● What did the exploit achieve? -Guessing his password gavea us limited access to the system as well as a login to the MySQL database. Which allowed us to find the password hashes for another user.
● Include a screenshot or command output illustrating the exploit
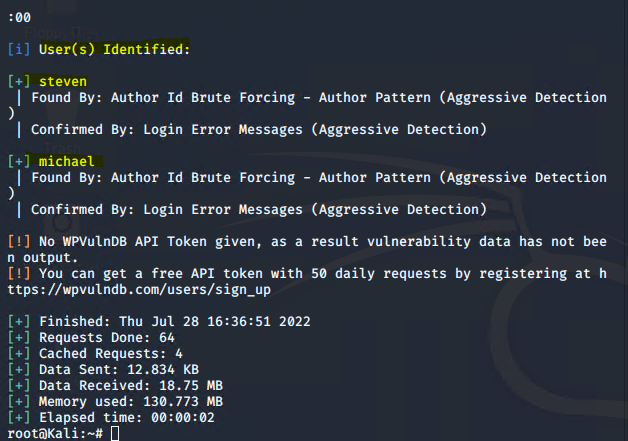
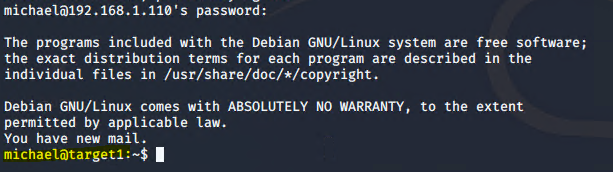
Exploitation: MySQL Database Access
Summarize the following:
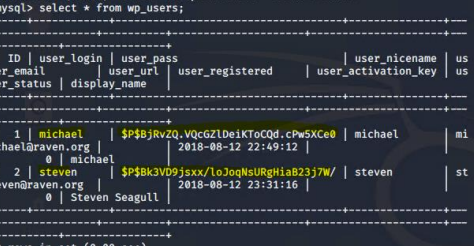
● Used Michael’s privileges to locate the MySQL username and password for the WordPress site database
● Gained root access to the MySQL Database
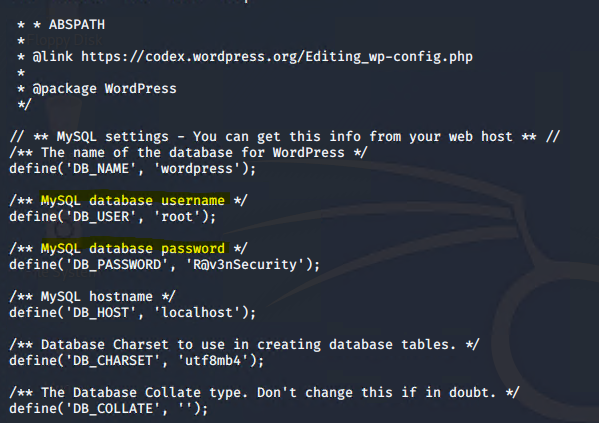
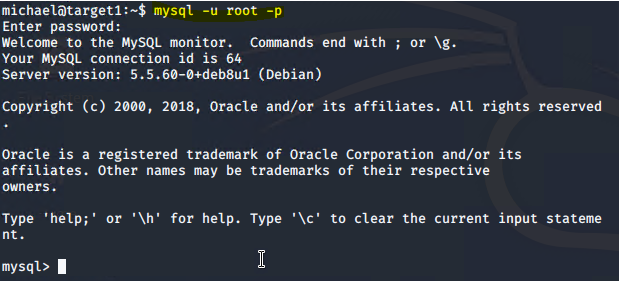
Exploitation: My SQL Data Exfiltration
Summarize the following:
● MySQL database enumeration and queries
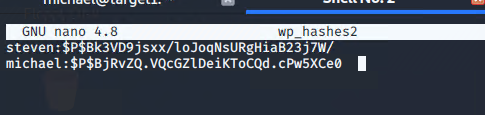
● Discovered the password hashes for Michael and Steven and saved them to a wp_hashes.txt file to be cracked via John the Ripper
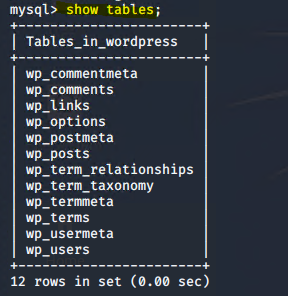
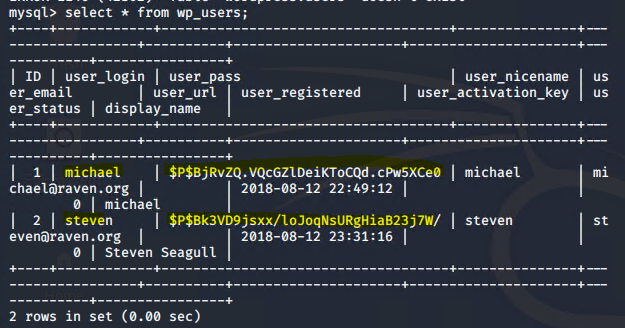
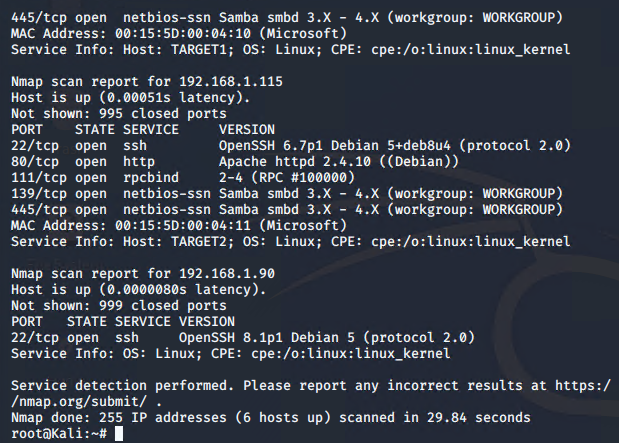
Stealth Exploitation of Network Enumeration
Monitoring Overview
● Which alerts detect this exploit? ○ WHEN sum() of http.request.bytes OVER all documents is ABOVE 3500 for the last 60 seconds
● Which metrics do they measure? ○ Packets requests from all the same source IP to all destination ports
● Which thresholds do they fire at? ○ Requests must exceed 3500 hits for longer than 60 seconds
Mitigating Detection
● How can you execute the same exploit without triggering the alert? ○ Only target known ports that can be a vulnerability
● Are there alternative exploits that may perform better? ○ Limit the number of HTTP requests that are sent within the 60 second window
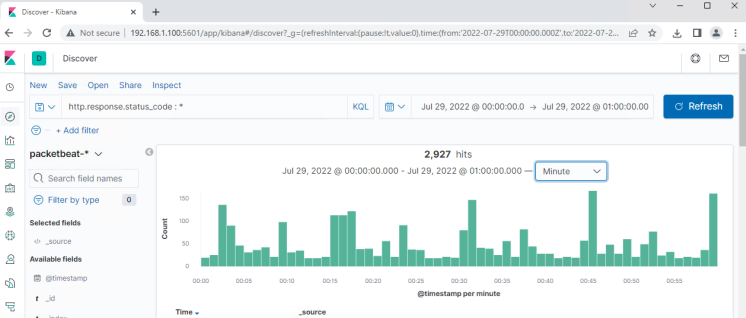
Stealth Exploitation of WordPress Enumeration
Monitoring Overview
● Which alerts detect this exploit? WHEN count() GROUPED OVER top 5 ‘http.response.status_code’ IS ABOVE 400 FOR THE LAST 5 minutes
● Which metrics do they measure? HTTP error code 401 that may indicate an attacker
● Which thresholds do they fire at? Above 400 HTTP responses over a 5 minute period
Mitigating Detection
● How can you execute the same exploit without triggering the alert? Pause for 1 minute after every 100 HTTP requests
● Are there alternative exploits that may perform better? Use command line sniffing instead of a program like wpscan
Stealth Exploitation of Password Cracking
Monitoring Overview
● WHEN max() OF system.process.cpu.total.pct OVER all documents IS ABOVE 0.5 FOR THE LAST 5 minutes
● CPU Processes
● Above .5 per every 5 minutes
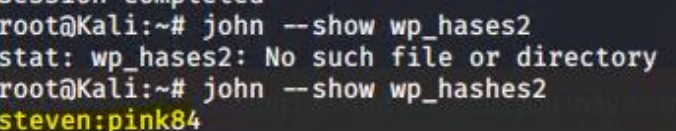
Mitigating Detection
● How can you execute the same exploit without triggering the alert? Instead of using John on the target machine, move wp_hashes.txt onto your local machine so that it uses your own CPU
● Are there alternative exploits that may perform better? Hashcat because it uses GPU instead of John the Ripper which uses CPU