Network Forensics Analysis Report
Time Thieves
You must inspect your traffic capture to answer the following questions:
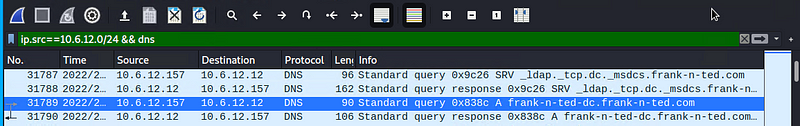
- What is the domain name of the users’ custom site? frank-n-ted.com
- What is the IP address of the Domain Controller (DC) of the AD network? 10.6.12.12
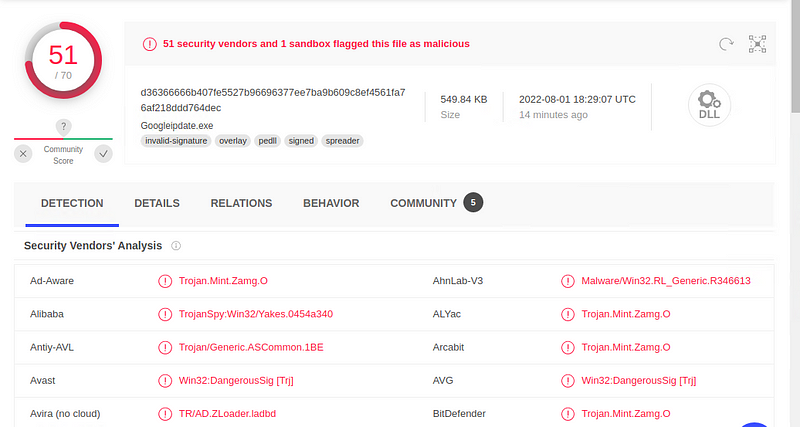
- What is the name of the malware downloaded to the 10.6.12.203 machine? june11.dll
- Once you have found the file, export it to your Kali machine’s desktop. Upload the file to VirusTotal.com.
- What kind of malware is this classified as? Trojan
Vulnerable Windows Machine
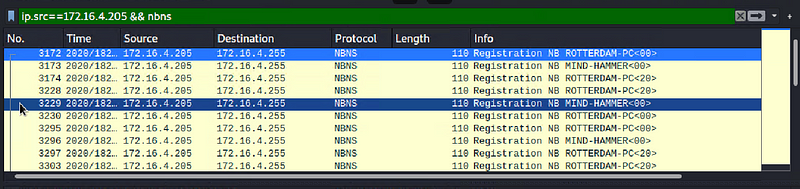
- Find the following information about the infected Windows machine:
- Host name ROTTERDAM-PC
- IP address 172.16.4.4
- MAC address 00:59:07:b0:63:a4
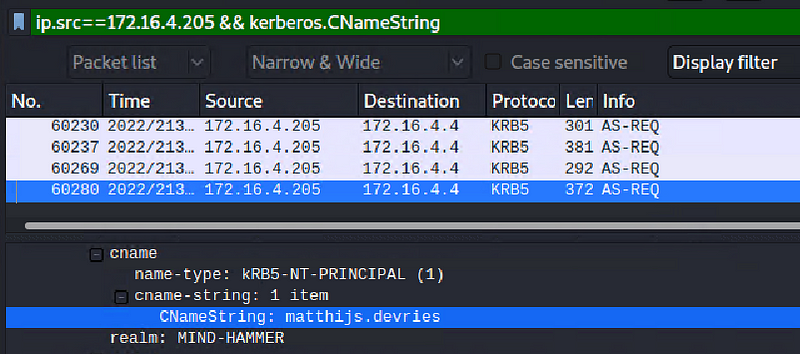
2. What is the username of the Windows user whose computer is infected?
This website offered a Windows user account from Kerberos traffic https://unit42.paloaltonetworks.com/using-wireshark-identifying-hosts-and-users/
So, the username is: matthijs.devries
3. What are the IP addresses used in the actual infection traffic?
185.243.115.84
As a bonus, retrieve the desktop background of the Windows host.
Hackertarget.com gives a cheetsheet on finding an image, There were only a few files that were worth considering because of the size of the files. This one actually looks like a screenshot of a desktop
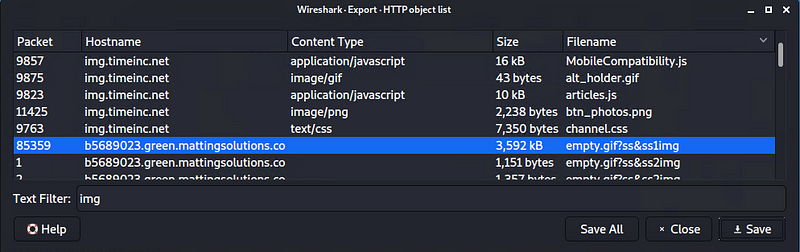
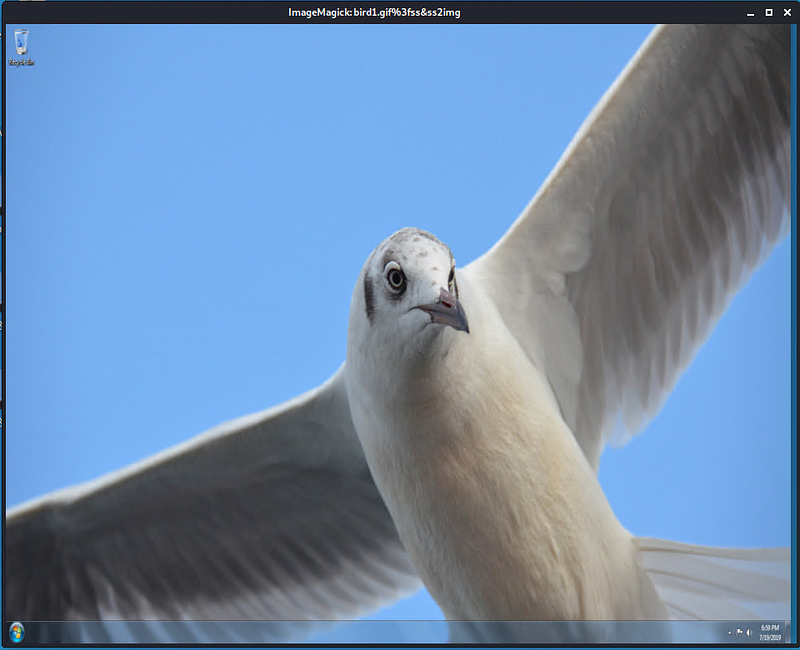
Illegal Downloads
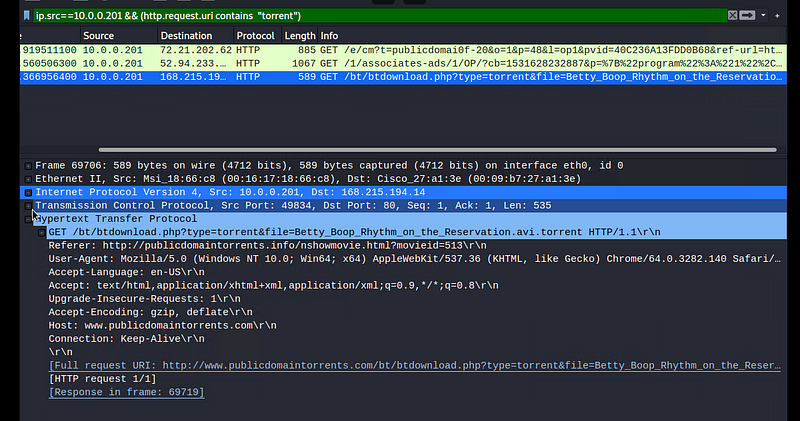
Find the following information about the machine with IP address 10.0.0.201:
MAC address 00:16:16:18:66:c8
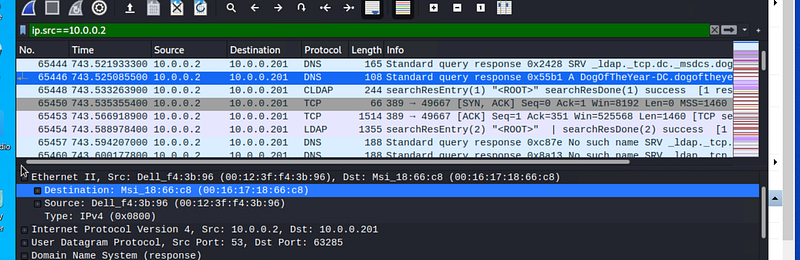
Windows username elmer.blanco
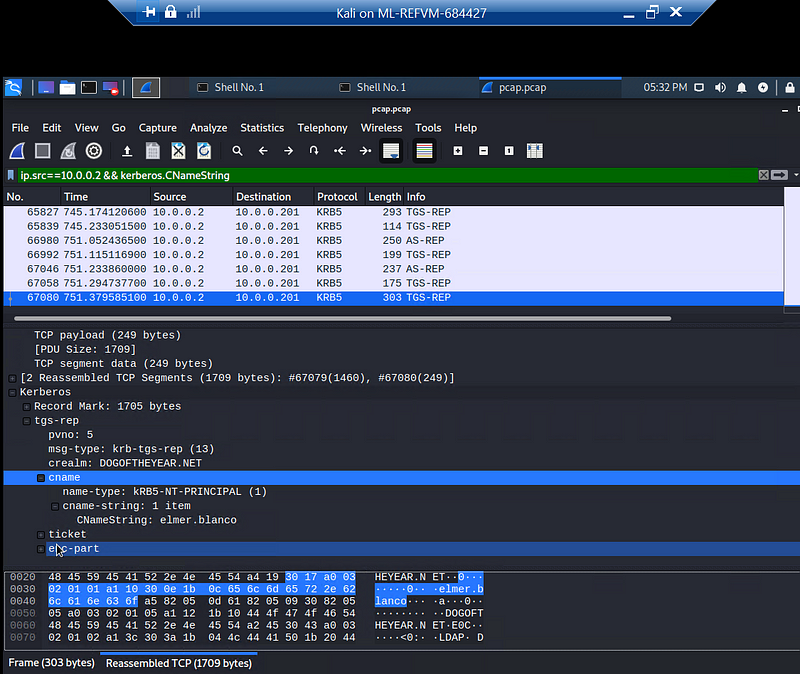
OS version Windows NT 10.0
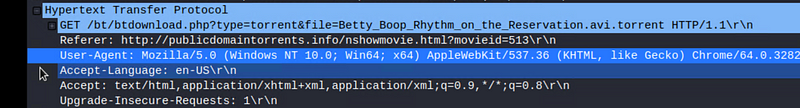
Which torrent file did the user download? Betty_Boop_Rhythm_on_the_Reservation.avi.torrent