Crack a WPA Key

Steps used to crack WPA key are as follows:
Log into Kali and make a dir to store capture files. In the terminal, type the command man airmon-ng. This command creates a interface that can be used to monitor all wireless traffic to carry out the attacks. The airmon-ng tool is used to enable the monitor mode on wireless LAN interfaces. It may also be used to toggle between the monitor mode and the managed mode. Entering the airmon-ng command without parameters will show the interface’s status on the WLAN.
Verify the interface has been created by running ifconfig. You will see there is no IP listed. Open a new terminal and enter the command airplay ng -05 -a then the target MAC -H then the host MAC on mon 0 or ylan 0 and –ignore — negative -on mon 0. The airplay -ng tool is used to inject frames to generate traffic that aircrack -ng will use to crack the WEP and WPA PSK keys. The commands listed will cause a DoS attack and you will be able to capture the client’s authentication information and reveal the network name.
We then open a new terminal and type airodump-ng -channel 11 –bssid then MAC of target then — right capture Mon zero. The airodump-ng tool is used for packet capturing of raw 802.11 frames and is particularly suitable for collecting WEP initialization vectors with the intent of using them with aircrack-ng. With a GPS receiver connected to the computer, airodump-ng is also capable of logging the coordinates of the access points that have been found. Additionally, airodump-ng creates files containing the details of all access points and clients found on that WLAN, similar to an IP discovery after an Nmap scan. The command monitors channel 11 and uses the MAC of target. Then it dumps all traffic from mon) into the new capture file.
We then do the airplay -ng command but increase the number of packets sent. Return to the airodump -ng terminal to then stop the dump process. The next command is aircrack-ng -w word list capture 01.CA p. This command will use the wordlist against the capture files to search for possible passphrases for the network. The aircrack-ng tool is an 802.11 WEP and WPA-PSK key cracking program that can recover keys when enough data packets have been captured. We will be cracking silent valor option 18. Type 18 and the capture file will compare keys against the wordlist. Once it has found the passphrase (dark obsidian), we can stop the interface with the command airmon-ng stop Mon zero.
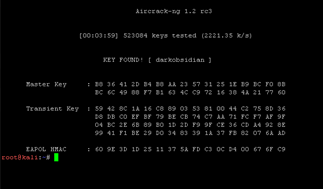
The time it took to identify the key is 3 minutes and 59 seconds.